Overview
RHQ has a simple and straightforward authorization model. It is used to both control access to a resource as well as specify what a user can do to that resource assuming access is granted.
Concepts
The following describe the concepts related to the RHQ security/authorization functionality.
Authorization Model
Permissions are set on a role. A role has:
-
One or more groups associated with it
-
One or more users associated with it
A role, therefore, grants its associated users with a fixed set of permissions to operate on its associated groups of resources.
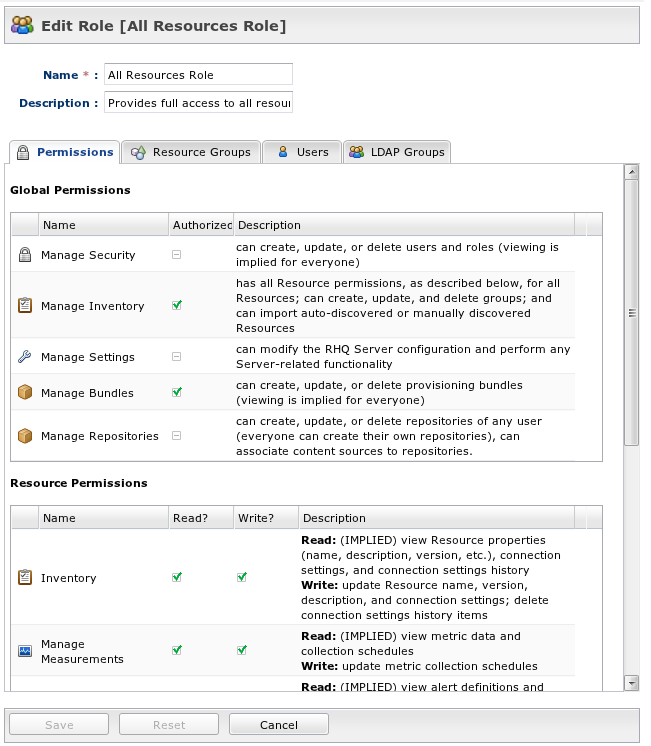
Permissions
Security permissions are separated into two types - global and resource.
Global permissions grant authorization across large parts of the RHQ system. Resource permissions give authorization only to those resources found in the groups assigned to the role.
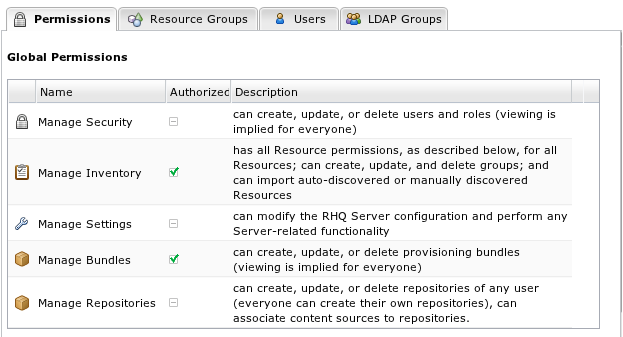
Global Permissions
-
Security - Allows the user to modify security settings (e.g. create, modify delete and assign roles) and it allows the user to create, modify and delete other users. This is considered the "superuser" role because once a user is given the security global permission, that user essentially has or can have access to the entire system (because, even if the user doesn't currently have any other permission or role assigned to him, he is free to add himself to any role and assign himself any other permission). Because of this, you must be very restrictive on who is authorized with this global security permission. Typically, if you give a user this global security permission, you also give that user all other global permissions.
-
Inventory - Allows the user to perform any task on any resource. Having a role with this permission grants the user to add, delete, configure, control and modify any resource, regardless of what other roles and associated groups of resources the user has been given access to. This is also the permission required in order to be able to import new resources into inventory.
-
Settings - Allows the user to view or modify the RHQ Server's administration settings.
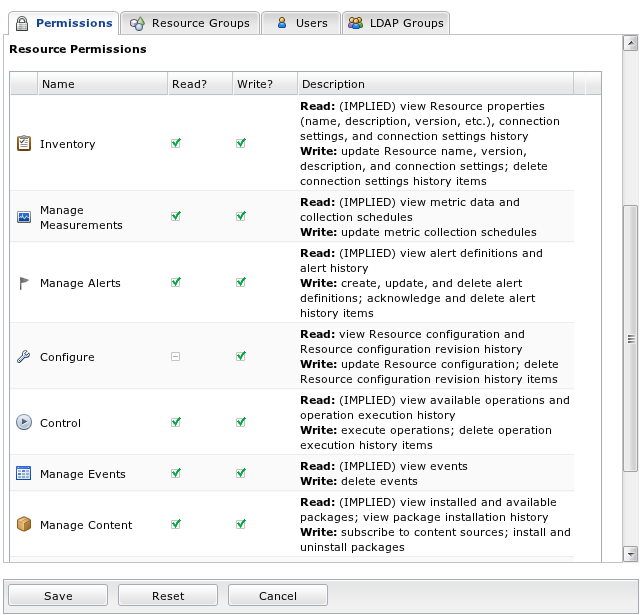
Resource Permissions
-
Modify - Allows the user to change information about the resource (its name, for example). This does not include being able to modify the configuration of the managed resource itself, this is only to modify the RHQ resource as it is represented in the RHQ inventory. (see the Configure permission below)
-
Delete - Allows the user to delete a resource from inventory.
-
Create Child - Allows the user to create child resources under another resource.
-
Alerts - Allows the user to create and modify alerts for a resource.
-
Measurements - Allows the user to modify the way measurements are collected for a resource.
-
Content - Allows the user to manipulate content related to a resource.
-
Control - Allows the user to execute operations (aka control actions) on a resource.
-
Configure - Allows the user to view and modify the configuration of the actual managed resource. This is different from Modify permission in that this permission actually allows you to change the settings within the actual remote resource being managed (for example, "Modify" permission would allow me to change the name of my JBossAS Data Source service resource as it appears in the RHQ GUI Console; the "Configure" permission allows me to change the actual JNDI name of my Data Source as it is deployed in the JBoss Application Server).
System Defaults
There is a default rhqadmin user that is a member of a system superuser role that provides full access to everything. This role cannot be modified.
There is also an "all resources" role which provides full access to all resources in the inventory. However, it cannot modify users, roles, or RHQ settings.